Ensuring Business Resilience
Disaster recovery planning involves the development of strategies, policies, and procedures to enable an organization to recover and restore critical functions and data in the aftermath of a disaster. The goal is to minimize the impact of the disruption on the organization's operations and stakeholders.
In today's interconnected digital landscape, businesses face a myriad of risks that can disrupt operations and compromise critical data. Whether it's a natural disaster like a hurricane or earthquake, or a malicious cyberattack aimed at crippling infrastructure, the importance of having a robust disaster recovery plan cannot be overstated. Such a plan not only helps minimize downtime but also ensures the continuity of business operations even in the face of unforeseen circumstances.
Disaster recovery planning involves the development of strategies, policies, and procedures to enable an organization to recover and restore critical functions and data in the aftermath of a disaster. The goal is to minimize the impact of the disruption on the organization's operations and stakeholders.
Key Steps of an Effective Disaster Recovery Plan:
1. Risk Assessment
The first step in developing a disaster recovery plan is to conduct a thorough risk assessment. This involves identifying potential threats and vulnerabilities that could disrupt business operations. These threats may include natural disasters such as floods or earthquakes, as well as human-made events like cyberattacks or infrastructure failures.
2. Business Impact Analysis
Once the risks have been identified, the next step is to conduct a business impact analysis (BIA). This involves assessing the potential impact of each identified risk on the organization's critical functions, processes, and resources. By understanding the potential consequences of a disaster, organizations can prioritize their recovery efforts and allocate resources more effectively.
3. Establishing Recovery Objectives
Based on the results of the risk assessment and BIA, organizations can establish recovery objectives for each critical function and process. These objectives should outline the desired outcomes of the recovery efforts, such as the maximum allowable downtime and data loss.
4. Developing Recovery Strategies
With recovery objectives in place, organizations can then develop strategies to achieve them. This may involve implementing backup and recovery solutions, establishing redundant systems and infrastructure, and developing communication and notification procedures.
5. Plan Documentation and Testing
Once the recovery strategies have been developed, it's crucial to document them in a comprehensive disaster recovery plan. This plan should outline the roles and responsibilities of key personnel, the steps to be followed in the event of a disaster, and the resources required for recovery efforts. Additionally, regular testing and validation of the plan are essential to ensure its effectiveness and identify any gaps or deficiencies.
Implementing the Plan
Implementing a disaster recovery plan requires ongoing commitment and collaboration across the organization.
Key steps in the implementation process include:
Training and Awareness: Ensure that all personnel are trained on their roles and responsibilities in the event of a disaster. Regular training exercises and drills can help reinforce these procedures and ensure that employees are prepared to respond effectively.
Monitoring and Maintenance: Continuously monitor the effectiveness of the disaster recovery plan and update it as necessary to reflect changes in the organization's environment, such as new technologies, processes, or threats.
Collaboration with Stakeholders: Work closely with internal and external stakeholders, such as vendors, partners, and regulatory agencies, to ensure alignment and coordination in disaster recovery efforts.
Conclusion
The ability to recover quickly from unexpected disasters is essential for business continuity and resilience. By developing and implementing an effective disaster recovery plan, organizations can minimize downtime, protect critical data, and ensure the continuity of operations even in the face of adversity. Investing time and resources in disaster recovery planning today can pay dividends in the future by safeguarding the organization's reputation, assets, and competitive advantage.
Integrity Solutions Group Welcomes Thomas Khoury
Integrity Solutions Group welcomes Thomas Khoury Senior Network Engineer to our Team!
Thomas joins Integrity with over 15 years of experience in Network Administration and IT Support within both the Healthcare and private business sectors. Thomas holds a Bachelor of Science in Information Technology as well as a Bachelor of Music.
Integrity Solutions Group welcomes Thomas Khoury Senior Network Engineer to our Team!
Thomas joins Integrity with over 15 years of experience in Network Administration and IT Support within both the Healthcare and private business sectors. Thomas holds a Bachelor of Science in Information Technology as well as a Bachelor of Music.
In Thomas's free time, he enjoys playing pickleball at a high level and spending time with family and friends. With Thomas's added expertise we look forward to continuing to serve your IT needs!
As always - We appreciate your business!
Thank you for your support!
How End of Life (EOL) Technology Impacts Your Business
Technology powers your business, but when software or hardware reaches its End of Life (EOL), it can quickly become a liability.
Technology powers your business, but when software or hardware reaches its End of Life (EOL), it can quickly become a liability. Recent EOL milestones, such as Microsoft Windows Server 2012 (October 2023) and Microsoft Office 2016 (April 2023), highlight the urgency of staying ahead of such changes. Looking forward, Microsoft Windows 10 will reach EOL in October 2025, and businesses must prepare now to avoid vulnerabilities and disruptions.
Here’s what you need to know about EOL and how it could affect your business.
What Is End of Life?
When a product reaches EOL, its manufacturer no longer provides:
Updates to enhance performance or fix bugs
Security patches to protect against cyber threats
Technical support to address issues or failures
Without these essential services, EOL products expose businesses to security breaches, system failures, and non-compliance with regulations.
Why Does EOL Matter?
Relying on outdated technology comes with significant risks:
1. Security Threats
EOL products are highly vulnerable to cyberattacks because they no longer receive critical security updates. Hackers actively exploit these weaknesses, putting your sensitive data at risk.
2. Operational Disruption
With no manufacturer support, an unexpected failure in EOL software or hardware can bring operations to a halt.
3. Regulatory Compliance Issues
Many industries have strict guidelines requiring up-to-date technology. Outdated systems can lead to penalties, fines, or loss of certifications.
What’s at Risk in Your Business?
At Integrity, we help businesses assess their technology to identify EOL risks. Common components that may need upgrades include:
Practice management and imaging software critical to daily operations
Network infrastructure like routers and servers
Operating systems such as Windows 10
By proactively identifying these risks, you can avoid costly surprises down the road.
How Integrity Can Help
Transitioning from EOL technology doesn’t have to disrupt your business. Integrity offers a comprehensive approach to managing EOL milestones:
System Assessments
We’ll evaluate your current setup to identify outdated software and hardware.Strategic Planning
Our team recommends tailored upgrades to meet your business needs and budget.Seamless Implementation
We ensure a smooth transition to minimize downtime and keep your operations running smoothly.
Start Preparing Today
With Microsoft Windows 10’s EOL on the horizon in October 2025, now is the time to plan your next steps. Don’t wait for security risks or operational disruptions to force your hand. Schedule a consultation with Integrity today to create a proactive plan that keeps your business secure, compliant, and efficient.
Stay ahead of EOL milestones—your business depends on it.
Could One Wrong Click Cost Your Practice a Million Dollars or More?
Disaster recovery planning involves the development of strategies, policies, and procedures to enable an organization to recover and restore critical functions and data in the aftermath of a disaster. The goal is to minimize the impact of the disruption on the organization's operations and stakeholders.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Strengthen your healthcare organization's resilience to emerging threats with Black Talon Academy's comprehensive Cybersecurity Awareness Training.
Our interactive training program includes real-world examples, stimulating exercises, and covers essential topics such as phishing, social engineering, password security, data protection, and more.
We have trained tens of thousands of doctors and team members on cybersecurity threats, which has prevented many organizations from falling victim to hackers.
Did you know?
Annual employee cybersecurity awareness training is required under the HIPAA security rule.
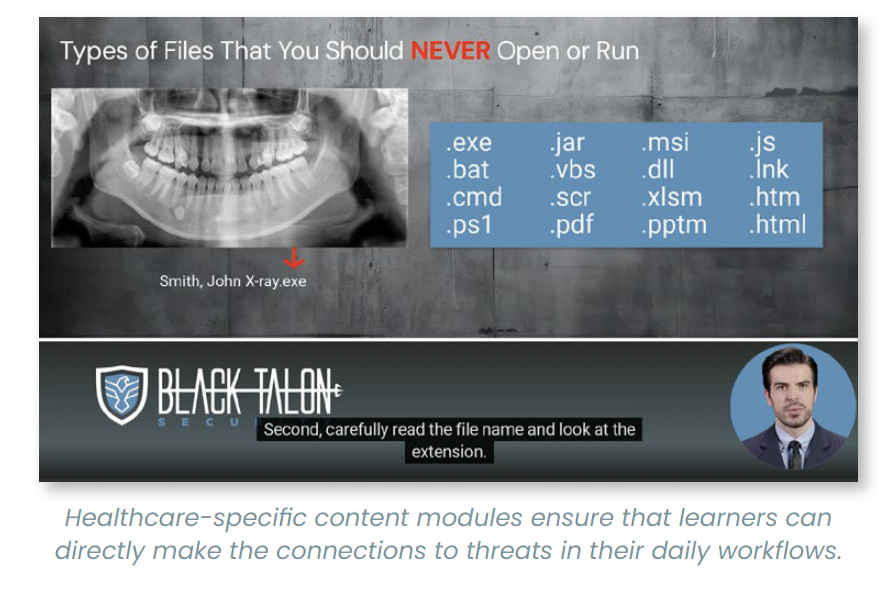
Our robust cybersecurity training program significantly reduces your "click-risk" and empowers your staff to recognize well-disguised malicious attempts to breach your network.
Key Features of Black Talon Academy:
COMPREHENSIVE VIRTUAL TRAINING
From identifying different types of cyber threats to practicing safe browsing habits, employees will be prepared to make good decisions and protect sensitive information from falling into the hands of criminals. Earn 1.5 CE Credits.
AFFORDABLE, SCALABLE SOLUTION
Our solution is cost-effective for any size healthcare practice or group.
SIMULATED PHISHING TESTS
We send simulated emails to your doctors and team members to test their awareness. Admin access is provided for full analytic reports of the results.
FREE HIPAA COMPLIANCE TRAINING
Included in the Black Talon Academy too.
Earn .5 CE Credits.
DASHBOARD MONITORING
Easily track your staff's training progress to ensure everyone remains up to date on the latest security protocols and compliance.
Make it stand out
Whatever it is, the way you tell your story online can make all the difference.
Significantly reduce your practice's cyber risk of a debilitating attack
by cultivating a culture of awareness. Black Talon Academy is your
frontline defense in the ongoing cyber war. Empower your team, fortify
your defenses, and proactively protect with informed awareness.